This was back in 2015 when my management team at Cisco put together a Innovation and Incubation team with the goal of generating new revenue streams for Cisco Advanced Services. The charter was to Identify the technology transitions happening at that time, their relevance to Cisco and If it makes sense start building professional services around it. So the technologies that were Identified was WebRTC, Security, Service orchestration and automation. A through market research and business impact assessment were performed by my team across each of these technologies to determine their feasibility from the business, technology and services perspective. It was determined that these were realizable goals.
Our team saw some low hanging fruits around collaboration security. What we saw that these services offered as freebie services to our customers by the field engineers around all 3 architectures (Unified Communications, Video and Contact Centers). We saw an opportunity to develop a structure around and offer this as a paid services to our customers. The new structure and the process would allow our customers to understand the security posture of their collaboration environment through the lens of a security framework. Remediation actions to improve the security posture then would be a seamless task.
Collaboration Application Landscape
The below diagrams depicts the applications, infrastructure and architecture for collaboration solutions. For the most part these applications were hosted on customers private data centers and some applications resided within the DMZ segment for certain functionality like b2b video communications.
So from a security standpoint these applications, infrastructure and the communications (voice and video) had to be protected from the bad buys

![Cisco Unified Contact Center Enterprise Design Guide, Release 10.0(1) - Deployments [Cisco Unified Contact Center Enterprise] - Cisco](https://www.cisco.com/c/dam/en/us/td/i/300001-400000/340001-350000/347001-348000/347368.eps/_jcr_content/renditions/347368.jpg)
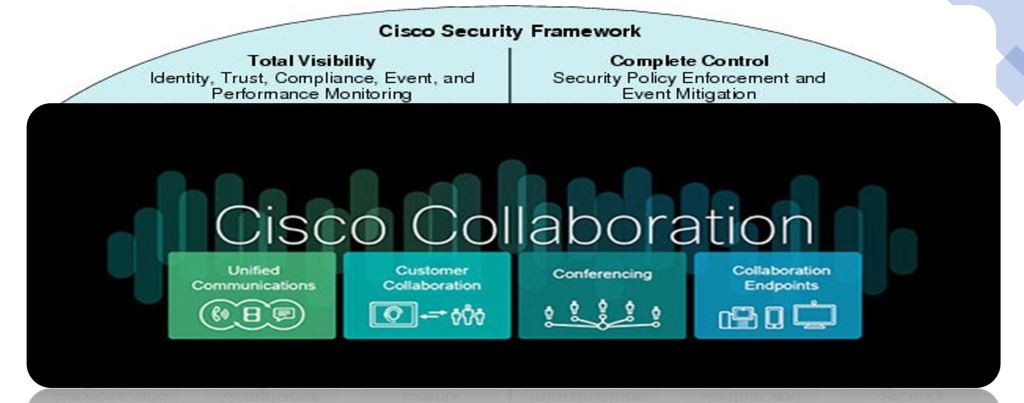
Security Framework
So given that we knew what we had to protect for Cisco’s customers, our next step was to apply a structure and process to assess the security posture. For this we leveraged a security framework that was already applied to other architectures like Networking and applied this to the Collaboration architecture.
The security framework gave use a new lens through which we could see how the security controls from the collaboration side would fit into this framework. The framework is also based on two key principles that is “total visibility” and “complete control” which goes with the notion that “if you cannot see it, you cannot control it”.

Mapping Security Controls to the Security Framework
Our next steps was to identify the security controls across all the applications and architectures for collaboration solution. over the next eight weeks, our team came up with more than 200 security controls. We then started to map these security controls to the Cisco security framework. In total we build three distinct security frameworks, one for Unified Communications, Video Collaboration and Contact Centers.
As an example, below you will see the security framework for Unified Communications applications and infrastructure where the critical security controls are being mapped into its framework categories.

A Reference Framework for Cisco Customers
The whole benefit of this exercise is that Cisco Collaboration customers especially their operations team now have a “reference” security framework for the solution that they are managing. Now they have a common language to speak with their enterprise IT security team and be able to explain the security posture of their environment. Secondly, Cisco engineers who are on field can do a security gap analysis for their customers and come up with remediation recommendation accurately and at a much faster pace.
Developing an Assessment Service for Launch
The heavy lifting has been done, that was to choose a framework, identify security controls and map them to a framework. Our next steps were the following:
- Build delivery process and methodology – Leverage cisco service lifecycle methodology
- Build delivery collaterals – Discovery, validation and report templates
- Train the service delivery teams – Leverage cisco NPI process
- Build sales decks
- Advocate the services with services sales
- Launch the service.
More on the above in my subsequent blogs…
More on the above in my subsequent blogs

Leave a comment